Analysis of the hacker attack on TV 5 Monde
On Wednesday April 8th French TV5 Monde was attacked and their transmissions were seized. Their social media accounts were used to spread the ids of French soldiers. How and why could this happened?
The cyber operation against the French TV channel is interesting out of several reasons. One is the technical aspect regarding the possibility to over take these kinds of systems to send messages. The second is the security political aspect regarding who the stakeholders are behind the attack, their purpose and motive, i.e. the how and the why. At the time of writing it should also be said that the information surrounding the event is scarce, which can affect the analysis of the actual course of events.
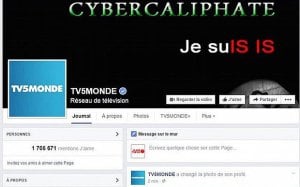 We started with trying to determine the purpose and goal regarding the operation and its possible execution. The first question was how it was done technically. How did they manage to get to the broadcasting platform? It turns out that there is a lot of information completely open for a technically savvy person to take part of, providing several alternative approaches.
We started with trying to determine the purpose and goal regarding the operation and its possible execution. The first question was how it was done technically. How did they manage to get to the broadcasting platform? It turns out that there is a lot of information completely open for a technically savvy person to take part of, providing several alternative approaches.
Its important to emphasize that the information used is publically available. We have not penetrated any of the systems. This also makes this analysis somewhat speculative based on our experience.
The first thing we noticed was that TV5 Monde has a lot of system exposed towards the Internet. Every system is a potential attack surface and a potential door leading to the back end systems. The more systems visible on the Internet, the more possible entry points for a hacker to attack.
A simple search pointed us in the direction of the broadcast platform used by TV5 Monde for its broadcasts, which by the way is Swedish. There are several possible ways to attack such a platform; you could go directly for the web management interface. This could be accessible from the Internet.
You could also try to attack the billing server. The billing server controls which program or channels that should be sent to the different distributors, If you could tell the billing server that no one uses the channel any more or worse, delete the customer database, then the broadcast will seize. With them saying that there were damages to the system, I would say that this is the most plausible approach.
So how did they manage to get to the server? There are several scenarios to answer this question, lack of patches, weak passwords, and non-existent perimeter protection. You have to keep in mind that TV broadcasting is about performance and storage, not security.
When performing security assessments of other TV companies there have been findings of the use of common users and passwords. Firewalls and patch routines have not been used. In this case the attacker also could have used a simple spearfish attack against the employees of TV5 Monde. With time we hopefully will get the full picture of the actual event.
Regarding the social media and the accounts used, those are relatively simple to over take. There’s usually a common account used by all communicators. The passwords are usually weak to make it easier to update with new tweets or statuses. If one account is taken the chances are that you are having them all.
Now that we understand the how, we would like to get a grip on the why. The why is as important to understand as the how, this so we can understand from what to protect ourselves. We have to threat model to make the right security decisions.
Who were those people attacking TV5 Monde?
The stakeholders in this operation uses wordings like cyber jihad, cyber caliphate and cyber terrorism. The expressions are viable in the mass media and follow IS (Islamic State) will to prove that they have the ability to act in both the physical world as in the information arena.
Generally you can say that cyber terrorism is a collective name of a lot of different activities in cyber space. Like “traditional” terrorism it all comes down to create fear and uncertainty, as well as showing that you have the means, motive and resources to conduct operations on the Internet. In this case to influence the opinion to choose side, i.e. a psychological operation.
At present we don’t know who is behind the operation. It could be a loosely connected network of hackers, so called hacktivists, who has coordinated their action with the purpose of supporting, IS ideologically. There are several groups like these with their background in the Middle East and who are working globally. Some of the members may very well live in Europe and in France.
It could also be more resourceful organization acting in the shadows with a completely different agenda than the one that meets the eye.
Objective
It looks to be at least two objectives. On the one hand it is the TV channel itself and its operations. The other is the French soldiers and the information regarding their supposed operations in Iraq and Syria. In news articles published about the event it is said that the cyber jihadists have the name as well as the CV on some of the soldiers, or alternatively the name of relatives of the military personnel. This information should supposedly have been published online. This information is now removed which makes it hard to verify.
The cyber jihadists purpose could be to threat and intimidate not just these individuals but also France and its allies. Ultimately one might want to lower the pressure that currently exists on the organization in Iraq and Syria by conducting attacks on French soil.
Intimidation is an important part of the logic of terrorism. It raises questions. Is it really true that they have access to that kind of information regarding the soldiers or is it bogus? If they do how did they come across it? Through insiders or maybe from social media where soldiers or their relatives out of thoughtlessness mentioned that they’re on mission in the area. This is unclear as of now. No matter what, this proves the need to protect vital information, especially when it comes to military personnel on mission.
What are the conclusions of this event?
The systems used by the TV channel are most likely vulnerable to digital attacks. The attackers purpose has been to prove that they have the resources, motive, will and means to coordinate and conduct psychological operations. Their actions will most likely continue. The consequences will thus be that we have to create awareness and contingency to handle these complex events.
This means among other things a need to develop the knowledge regarding threats and developing strategies and routines for security. Security should be a normal and welcome part of daily operations.
Our hope is that the responsible parties will publish an analysis, which describe the event. Such a report would be of great help in the work of requirements regarding the security levels on such a significant and important psychological symbol that a TV channel with global reach have.
Roland Heickerö & Patrick Kall
Roland Heickerö is security consultant at Knowit and adjunct Professor at the KTH – The Royal institute of technology in Stockholm. He is also the author of the book “The dark sides of the internet. On cyber threats and information warfare”
Patrick Kall is security consultant at Knowit who have over 20 years experience working with IT and information security, with advanced technical security solutions, network architecture, security assessments and strategic steering and advisory.
Knowit is one of the leading consultancy firms in the Nordic region and also the Nordic region's fastest-growing consulting firm in IT and information security. For more information, press here.
This analysis was first published in Swedish.

